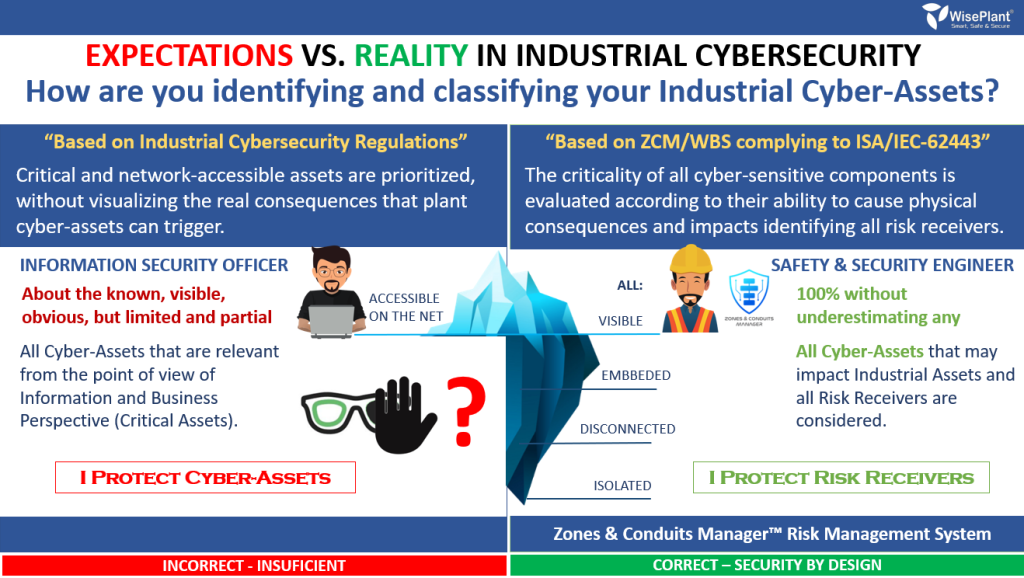
We continue to observe how many professionals with vast experience in Information Security, industrial companies that take action, renowned cybersecurity consultants, government organizations and technology developers are wrong (by far) when it comes to identifying, evaluating, classifying and managing industrial cyber assets. One of the main mistakes is to focus and prioritize those that have communications interfaces over those that do not. The errors we observe are many and very significant.
- Identify cyber-assets according to their communications interfaces.
- Classify according to their technological vulnerabilities.
- Not knowing the function of each cyber-asset.
- Obsession with the identification and management of vulnerabilities.
- Identify correctly according to its type and function.
- Classify according to their criticality towards risk receptors.
- Design and segment into zones and ducts.
- Prioritize based on inherent risk.
Incorrect: unfortunately, the vast majority of companies, including reputable consultancies, focus on the protection and computer security of industrial cyber components. They focus on the protection and security of the data and information they contain inside. Confidentiality is usually irrelevant, especially in those that are most critical and present the greatest dangers to the organization.
Correct: focus on the capacity that industrial cybernetic components have to cause consequences for all receptors of industrial risks in the event that they are compromised. The dangers in industrial cybersecurity are on the outside of physical assets and not on the inside. Understand the function that each one of all the cybernetically sensitive components fulfills in the industrial process in particular.
A serious mistake that the vast majority of organizations and that many professionals make is working on incorrect assumptions. Many think that if they protect data security, its integrity and availability are indirectly protecting and shielding risk recipients (who do not know who they are or why) from potential dangers. Industrial cybersecurity is not information security. The most serious and dangerous consequences are in the physical world and not in the computer world.
- They underestimate the criticality of cybernetic components that do not have communication interfaces.
- They prioritize those that are in the data processing centers over those that are in the extremes.
- They visualize cyber-assets by their communications interfaces.
- Obsession with vulnerabilities, even those that do not produce any real danger.
- They perform penetration tests, pentest.
- Classify according to the data and information they contain.
- They classify cyber-assets by their functionality and intrinsic characteristics.
- All cyber sensitive components are identified.
- Even those who are completely isolated without any kind of communication.
- They evaluate and classify based on their ability to cause harm to all risk receptors.
- All necessary and relevant information is captured.
- Risk recipients are more important than cyber-assets.





Get Involved & Participate!
Comments