Emphasizes the necessity of a continuous cultural change towards cybersecurity in industrial operations for end users, service providers, and manufacturers. It highlights the importance of implementing cybersecurity management programs, conducting risk assessments, mitigating risks, and maintaining long-term security measures across the entire supply chain.
Category: Insights
Episode 1 Clip 2 – What is the main difference between IT and OT security?
Discusses the significant differences between IT and OT security. It highlights key distinctions such as availability, technology lifespan, and the primary focus of preventing cyber incidents in IT and preventing consequences in OT environments. The crucial dissimilarity lies in managing risks: IT focuses on preventing incidents, while OT prioritizes preventing consequences.
Episode 1 Clip 1 – Tell us about yourself
Max shares his experiences working in the industrial automation field, collaborating with the International Society of Automation (ISA), and transitioning into cybersecurity. He highlights the importance of ISA standards in industrial automation and cybersecurity, emphasizing his active involvement in ISA activities and training programs.
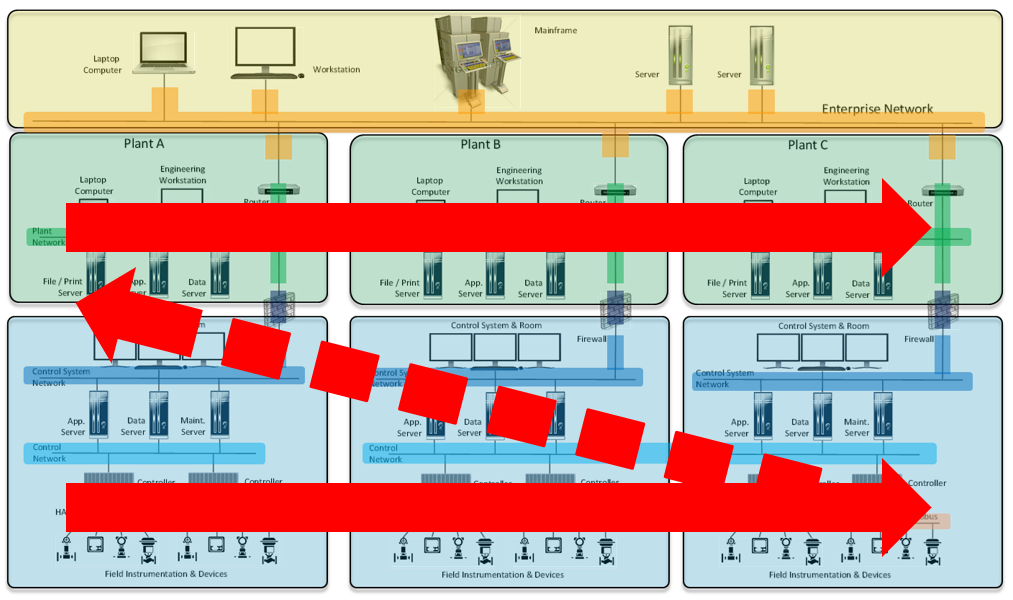
Understanding Zones and Conduits
Every professional who designs configure and maintain any type of control systems, need to learn about zones and conduits and manage the new security requirements and develop necessary skills according to their function, even if they are not into industrial cybersecurity.
The State of Knowledge and Risk Management in Industrial Cybersecurity (ISA/IEC-62443-3-2)
The state of knowledge in industrial cybersecurity during the past decade is based on a vast experience. There is a lot more to come soon.
Rationalization: Stop spending valuable resources wrongly
We see very often how companies (through their security staff) go shopping and rush to spend, often pushed by the pressure of the business, the inertia of the market, lack of knowledge, skill and opportunism of suppliers, before performing a good risk assessment.
Construction of Awareness and Training Programs
Currently, for companies it is a necessity to develop training and awareness programs in industrial cybersecurity, but there are doubts about how to successfully develop a program focused on generating the necessary knowledge, skills and actions for each type of public.
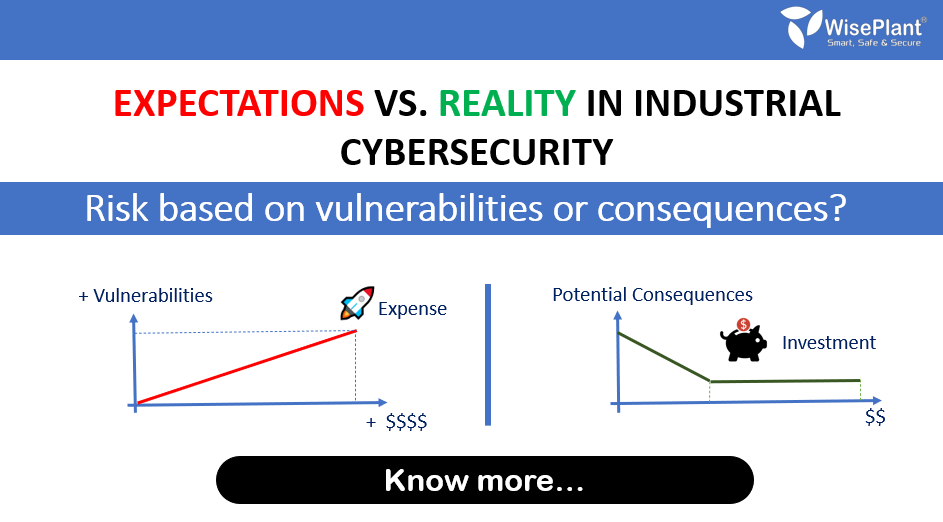
Industrial cyber risk management based on vulnerabilities or consequences?
We have already talked about the need to perform an industrial cyber risk analysis, and this time we will address one of the mistakes most commonly assumed "and accepted" by enthusiasts in industrial cybersecurity. Risk analysis based on vulnerabilities or consequences?
Working with future and new systems (Special Edition)
When the owner of the industrial plant has the possibility of having the best of both worlds, the best control systems and the best security. When the consequences occur the damage is done, and there is no turning back. That is why we say that it is never too late to deal with security (redesign), but the sooner much better (design).
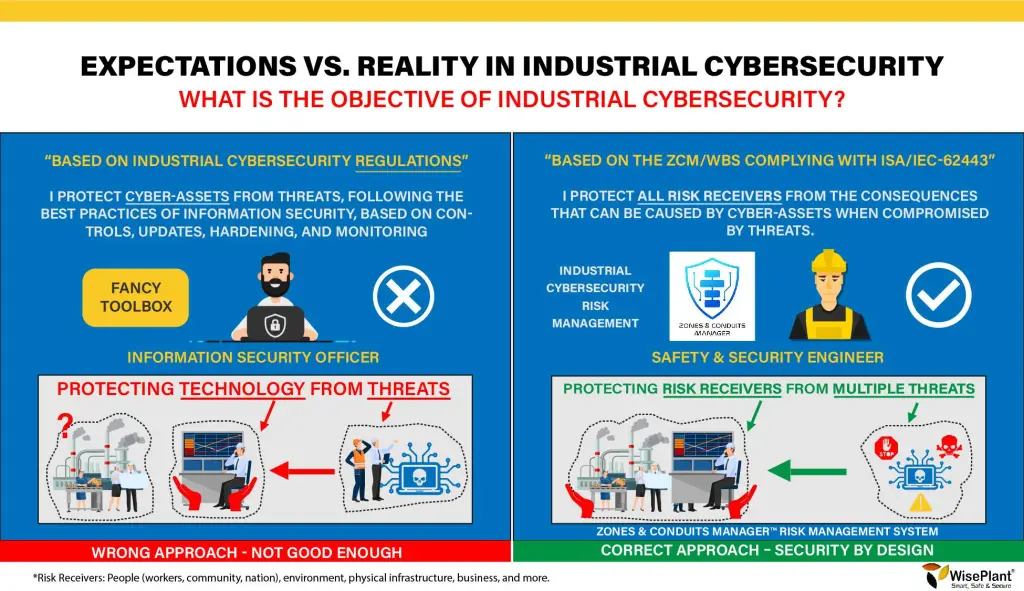
What is the Objective of your Industrial Cybersecurity Program?
We see how many professionals with vast experience in Information Security, industrial companies that take action, renowned cybersecurity consultants, government organizations and technology developers are wrong (by far) in defining the objectives for their strategy in industrial cybersecurity. Clearly defining goals is the first big step before we begin this big change.