Audit of Applications of the ISA/IEC-62443 series of standards.
This is one of the most relevant aspects in the application of the different standards for the verification that they are being implemented correctly and that the requirements are being met. Without losing the fundamental objective that is to “Mitigate Industrial Cyber Risk”.
What can be audited? What can be certified? How to audit? How to certify? How to prepare for an audit?
These are the questions we are going to try to answer in this article.
Roles in the ISA/IEC-62443 series of standards
The ISA/IEC-62443 series of standards is developed on three main roles. These are (a) plant owner, (b) value-added service provider, and (c) component and system manufacturers. Each with different responsibilities, concerns, priorities and objectives.
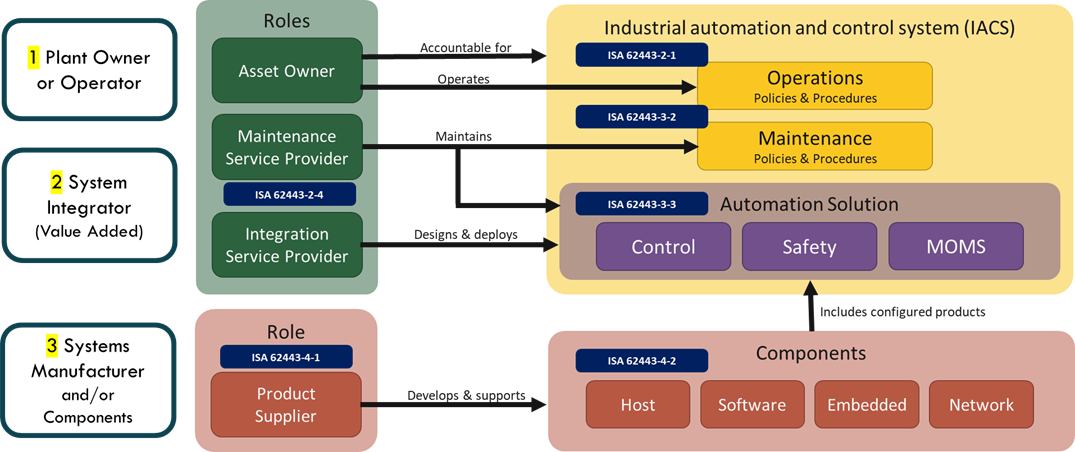
Figure 1. Main Roles and Responsibilities within ISA/IEC-62443 series of Standards
In the figure below you can see the ISA/IEC-62443 series of standards where it overlaps with the three main roles. Depending on the role, the level of responsibility for each of them will be and the security requirements that each one must develop and demonstrate to meet their responsibilities.
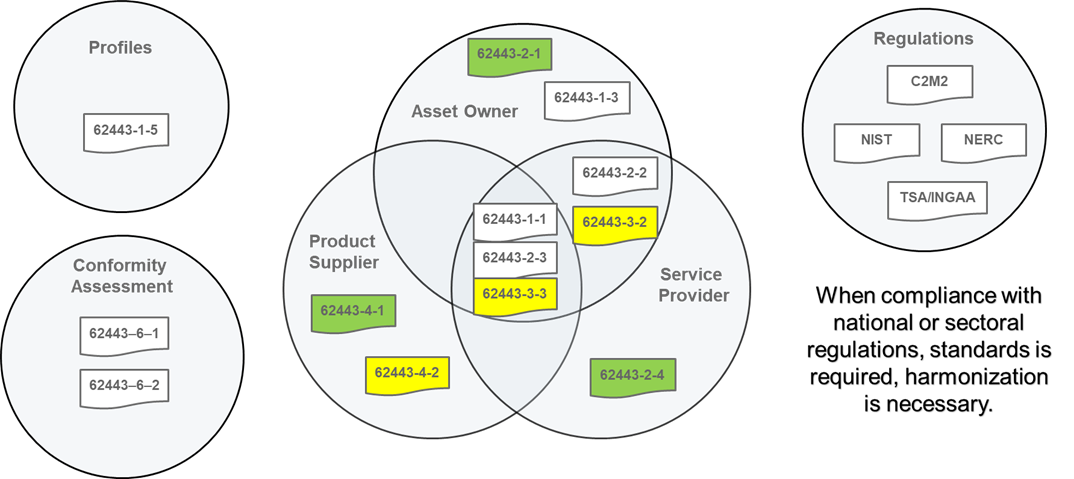
Figure 2. ISA/IEC-62443 series of Standards and Roles Relationships
Let’s analyze what can be audited and certified for each of the roles.
Role: Asset or Plant Owner
Certainly, the first thing that emerges is the industrial cybersecurity management system. (CSMS, Cyber Security Management System) or also called CSMP (Cyber Security Management Program).
It consists of the implementation of policies and procedures and all the demonstrations, or evidence, that it is being implemented and complied with correctly. More specifically, compliance with the requirements established in the ISA/IEC-62443-2-1 standard and those other standards that are of concern to the end user.
It can be audited and certified by the ISASecure recognized authority of certification. Keep in mind that not all of the recognized authorities audit and certify the same things.
The supplier management system. It is the responsibility of the plant owner to evaluate the capabilities of suppliers and demand the requirements that they must meet. Here we have two types of suppliers. These are:
These suppliers must develop a management system in accordance with the requirements of the ISA/IEC-62443-2-4 standard.
It can be audited and certified by the ISASecure recognized authority of certification.
The capabilities of product and system suppliers (manufacturers).
Component manufacturers must develop a management system that meets the requirements of the ISA/IEC-62443-4-1 standard.
It can be audited and certified by the ISASecure recognized authority of certification.
Systems under Consideration (SUC)
It is the responsibility of the plant owner to identify and define the multiple systems that make up the universe of systems covered by the ISA/IEC-62443 series of standards.
Solutions developed and maintained by value-added service providers.
In this case, the solutions must comply with the ISA/IEC-62443-3-2 and ISA/IEC-62443-3-3 standard, among other design requirements.
There are two basic types of these providers, which are:
System integrators for new systems.
Maintainers of existing systems. Sometimes it is the owner himself who maintains his industrial systems. These processes should be developed and implemented to meet some of the requirements from the ISA/IEC-62443-2-4. There will be synergy and overlapping with the other standards in the series.
This can be audited and certified, although the individual components are not certified or certifiable. Zones and conduits can be audited and certified to meet security requirements by design, produced following the risk assessment.
The Life Cycle of a given System under consideration (SUC). Each of the systems as identified by the owner will go through each of the three phases of the life cycle.
These phases are:
- Risk Assessment. Risks were identified and how these need to be mitigated.
- Design and Implementation. The security requirements have been correctly incorporated and the corresponding acceptance tests have been carried out.
- Operation and maintenance. The safe operation of the plant is being assisted, and preventive and corrective maintenance activities are being carried out.
Each of the phases can be audited and certified. The next phase should not be started if the previous one has not been completed or completed correctly. Many are not following this recommendation, ignoring fundamental key steps in the process.
Components Capabilities
In this case, the components must comply with the requirements established in the ISA/IEC-62443-4-2 standard.
This can be audited and certified. Many times, components that are not certified are required to be audited to know and confirm their actual security capabilities. Compliance with the specific SLC will be irregular, but still need it to determine the SLA of the zones and conduits.
Personnel Knowledge & Expertise
Knowledge of the ISA/IEC-62443 series of standards through the IC32, IC33, IC34, IC37 and IC47 courses. They aim to develop and certify knowledge. These courses are more for specialized users and experts. They are not for all the personnel of the organization.
Knowledge of CSMS/CSMP management methodology. If WisePlant’s WBS Cybersecurity Lifecycle Methodology is used then the courses EN50, EN60, EN61, EN62, EN99 and 2170 will be good enough. They aim to develop and certify practical expertise. These courses are for everyone, even for those who do not have a deep knowledge of the ISA/IEC-62443 series of standards.
Role: Value-Added Service Providers
There are several types of value-added service providers. Basically, we have the system integrator that supplies turnkey solutions, which are installed in an industrial plant. We call these systems new or future.
There are also service providers on existing systems already installed that can be very old systems, in many cases they are maintained in the plants for decades.
Component manufacturers also provide value-added services. To a lesser extent, but they also do. Generally associated with maintenance, update, patch application, among others.
In the case of system integrators, they must develop the capacity to budget, design, purchase, assemble, configure, test, install, ensuring that they will meet the security requirements for each zone and conduit. The system integrator must incorporate “security by design” into its engineering processes to ensure that security requirements will be met and to ensure that the following situations occur:
Select hardware and software components wisely. Once these have been selected and purchased, if these components are not the right ones, the project will be greatly damaged, with delays, repurchase, economic losses, penalties, etc.
Configure the components correctly. Avoid having to redo the engineering of the system because at the end of the project they realize that the system does not meet the security requirements.
Succeed in C-FAT (Cyber-FAT, Cyber Factory Acceptance Tests) and C-SAT (Cyber Site Acceptance Tests) factory acceptance tests.
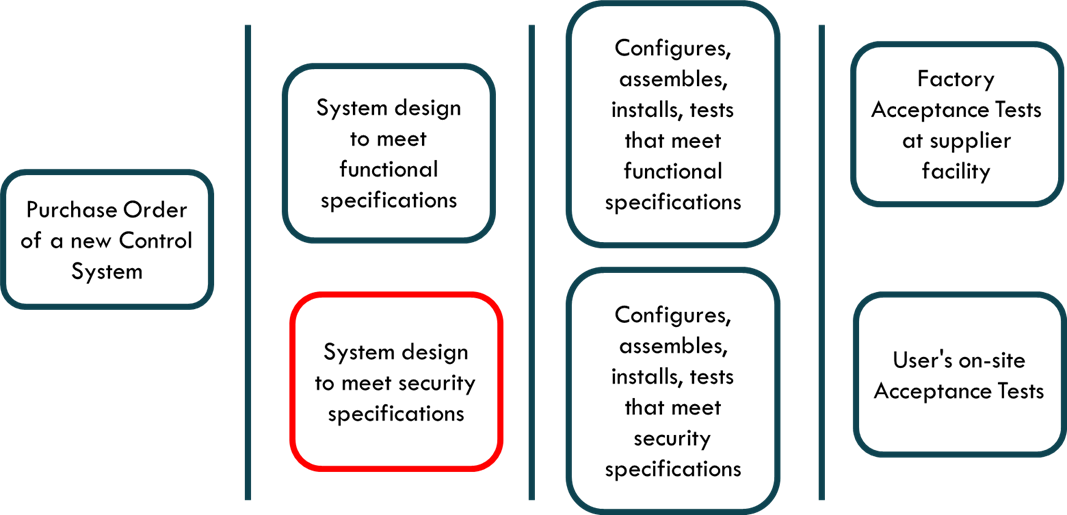
Figure 3. Working with Cybersecurity Requirement Specifications (CSRS)
The system integrator must have a management system ensuring that their engineering processes will build a system that works, as they have always done, but also meets the security requirements expected by their client.
Many companies believe that having engineers certified in ISA courses is enough. Although it is a very good initiative, this is incorrect. Having certified professionals is far from being a guarantee that the systems to be supplied meet security requirements. Without engineering-by-design processes, there’s no way to guarantee security success. Most likely, they will not succeed, unless the requirements are really very low or almost zero.
This is where the ISA/IEC-62443-2-4 standard comes into play. It defines twelve security domains with several requirements in each. The certification of professionals is only a requirement in the first domain. The first in the long list of requirements.
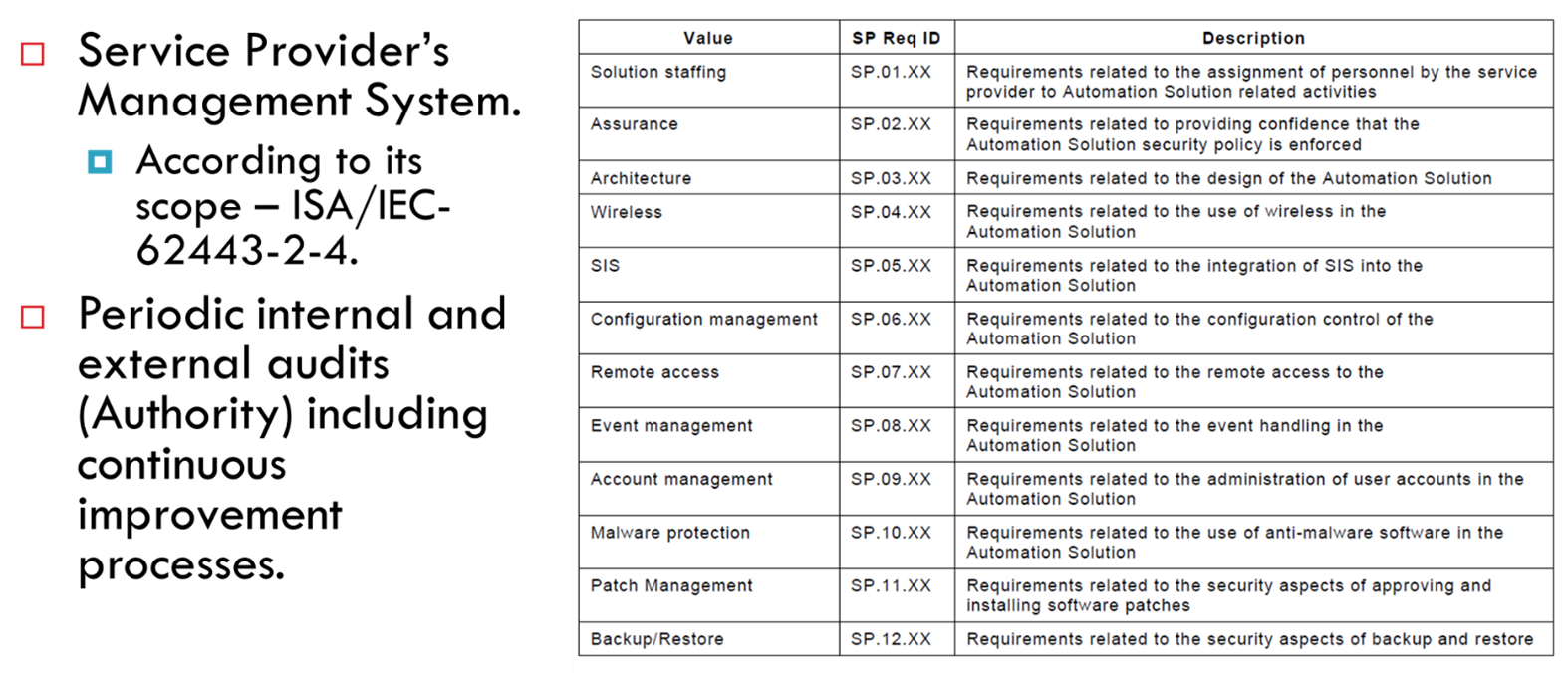
Figure 4. ISA/IEC-62443-2-4 – Requirements for Service Suppliers
This can also be audited and certified. It should be of great interest and concern to end users that their suppliers have a mature level of development of the ISA/IEC-62443-2-4 standard beyond certified professionals. They should know the SL-C of the systems they are supplying (even if they are not certified) among many other requirements. If the system does not meet the requirements of their customers, they should know in advance how they are going to compensate them to comply. This is before quoting.
This must also be managed through the procurement department of the Asset Owner. Evaluate your suppliers based on their ability to deliver. Stating in the specifications that the system must comply with the ISA/IEC-62443 series of standards, without specific security requirements is the same as nothing. Because any product can comply with ISA/IEC-62443 at SL=0. Whether the provider has certified professionals is the same thing. A risk assessment, a detailed design and a technical specification of security requirements (CSRS) must be produced.
The same goes for suppliers. They invest in training courses for their professionals, but they stay there. These professionals will one day leave the company. The supplier loses the investment. The supplier missed the opportunity to develop its processes that comply with the ISA/IEC-62443 series of standards and company-wide capabilities.
Vendors that develop industrial cybersecurity services around the ISA/IEC-62443 series of standards are no exception to the requirements. These suppliers must also have a documented practice with documented processes and templates that incorporate the requirements of the standards correctly and ensure quality and success in each of their projects without deviation. Currently, most of these suppliers are working ad-hoc and with engineering practices that do not comply with the ISA/IEC-62443 series of standards. They have a completely biased or distorted view of the set of requirements.
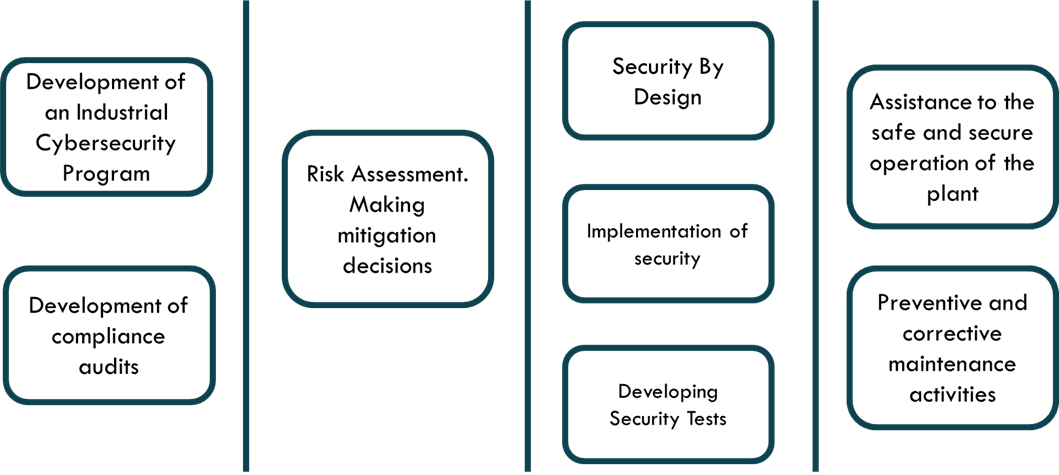
Figure 5. Industrial Cybersecurity Services Overview
The lack of knowledge of end users is a weakness that is being exploited by the business-hungry and also knowledge-hungry market to literally sell anything to their customers. This is even seen by well-known IT and OT services companies.
What we do and how we work?
At WisePlant we have developed a WBS methodology that serves both end users and providers of value-added services. We have even developed a methodology to develop audits. In this process we identify the control points. These checkpoints contain mandatory requirements of the ISA/IEC-62443 series of standards that, regardless of the particular methodology used, must be produced.
We worked for many years with ISA Secure. We are active members of ISA Secure. We know the standards deeply, and what the Authorities of Certification will do, how they will do it, and how they will request the evidence. They will investigate these Control Points as a baseline.
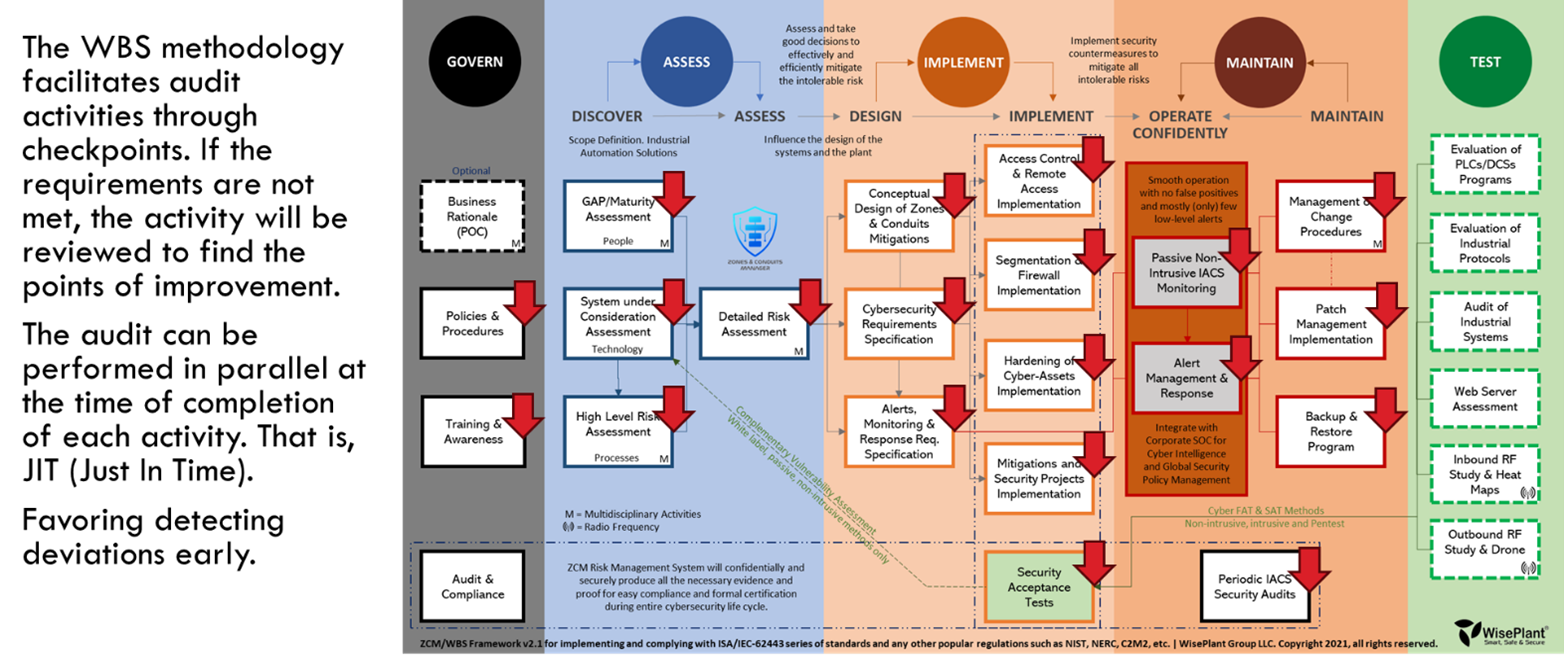
Figure 6. Wiseplant’s WBS Cybersecurity Methodology
Each of the control points serves to evaluate both the requirements of the end user or plant owner and the service provider. Using WisePlant’s WBS methodology shown in the figure can be audited and certified in two ways. At the end of the whole process or at the end of each of the activities. The second is the best option since it allows errors, failures and deviations to be detected early. Preventing the propagation of error in the project is of great added value for the parties.
Role: Components and Systems Supplier
This is for any company that manufactures hardware or software components or a combination of them to make up an industrial system.
Manufacturers must develop design, development, construction, and supply processes that meet the security requirements of the ISA/IEC-62443-4-1 standard. Management over the life cycle of the product from its initial conception, from the moment it was drawn on a paper napkin. If the product is not designed from the outset to meet a certain level of SLC security, it never will. It is not possible to meet the security requirements of the ISA/IEC-62443-4-2 standard by pure patching vulnerabilities. If the product is already on the market, it will hardly be certified. Perhaps with some low SLC such as SL=1 after a lot of effort and modifications. From SL=2 upwards they no longer have a chance.
To certify components that meet the security requirements of ISA/IEC-62443-4-2, they must first certify the management system to the requirements of ISA/EC-62443-4-1. This process can take several years. Many companies are working on it, but they have been in the process for years.
Many believe that the cybersecurity of a component depends on not having vulnerabilities. Not only is this misleading, but, if true, it would also be insufficient. The ISA/IEC-62443 series of standards goes much further.
This is taught in the official ISA IC47 course. Little known but highly recommended for component manufacturers. This course is not part of the IC32, IC33, IC34, and IC37 expert practitioner program.
A system may have vulnerabilities in its zones and conduits. A component in a zone or a conduit, can and does have several vulnerabilities. The important and fundamental thing that the vast majority lose sight of is that the industrial plant does not have risks. That intolerable consequences cannot occur. Even if the cyber incident ends up occurring. This is the true resilience.
The manufacturer must develop an industrial cybersecurity management program in accordance with the requirements of the ISA/IEC-62443-4-1 standard, which is developed on a series of good practices and procedures. These are summarized in the figure below.
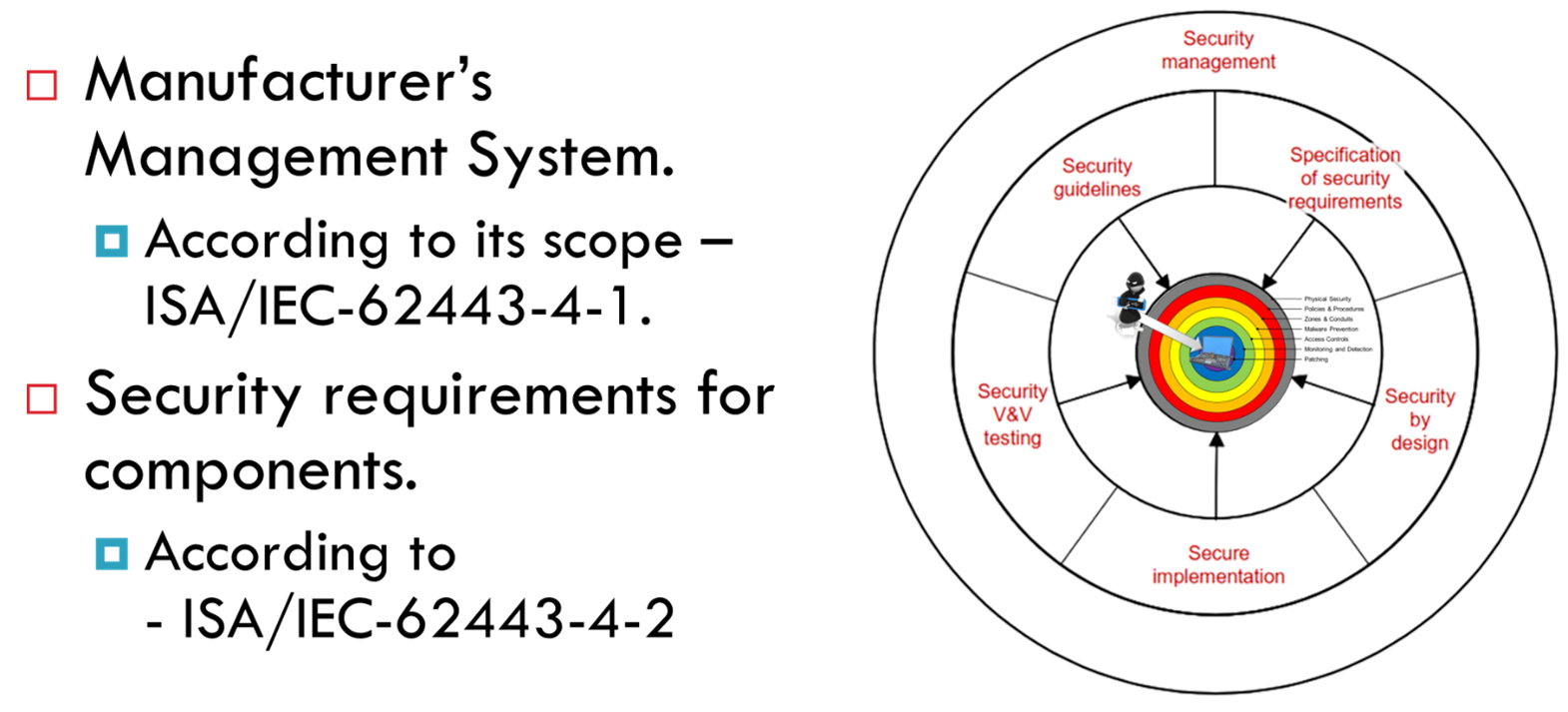
Figure 7. Product/System supplier Cybersecurity Lifecycle Management Requirements
The manufacturer’s management program, as well as the SLC safety level of the components being manufactured, can be audited and certified. In fact, this is also being done.
The WisePlant Solution
Our solution is based on three main pillars. These are:
- The RMS/ZCM System. All-In-One solution covering all the requirements of the ISA/IEC-62443 series of standards and complementary regulations (NIST, NERC, C2M2, etc.)
- The WBS Lifecycle Services.
- For End Users.
- For Value-Added Services Suppliers.
- The WBS Training Courses.
- The 2150/EN50, 2160/EN60, 2161/EN61, 2162/EN62, 2199/EN99, and 2170/EN70.
- And the official ISA courses. IC32, IC33, IC34, and IC37.







Get Involved & Participate!
Comments