Threat: it can be anything with a certain capability to compromise the confidentiality, availability, and or the integrity of one or more cyber-sensitive assets. In this context, threats can be natural, technological or entities. A few real examples below.

Ransomware Hits Critical Infrastructure Hard, Costs Adding Up
The article iscusses the rising threat of ransomware attacks on critical infrastructure, highlighting the economic toll, challenges in securing vital ...

FBI Warns: Chinese Hackers Are Preparing to Wreak Havoc on US Water System | Facts Matter
This is all part of the new global battlefield, where world powers don’t compete against each other directly using kinetic ...

Stealthy ‘sedexp’ Linux malware evaded detection for two years
Discover how the 'sedexp' Linux malware stayed hidden for two years, impacting detection and security protocols. Insights and strategies outlined ...

ICS malware FrostyGoop takes advantage of Modbus weakness, remains a threat to OT worldwide.
The malware leverages Modbus TCP communications to target operational technology assets — and can easily be repurposed to compromise other ...

BlackCat ransomware uses new ‘Munchkin’ Linux VM in stealthy attacks
BlackCat ransomware has been found to use a new Linux virtual machine called 'Munchkin' to launch stealthy attacks. Protect your ...

Building automation giant Johnson Controls hit by ransomware attack
Johnson Controls, a leading provider of building automation systems, has been hit by a ransomware attack, potentially compromising the security ...

Cuba ransomware uses Veeam exploit against critical U.S. organizations
"Cuba ransomware: Unleashing a Veeam exploit to wreak havoc on U.S. critical organizations." ...

Physical attacks on power grid surge to new peak – Power Grid Sabotage
People are shooting, sabotaging and vandalizing electrical equipment in the U.S. at a pace unseen in at least a decade, ...

CosmicEnergy ICS Malware Updates
CosmicEnergy ICS Malware is a sophisticated cyber-attack targeting industrial control systems. It is designed to steal data, disrupt operations, and ...

What is Evil PLC attack and how to prevent negative consequences on industrial plants
"Protect your industrial plant from Evil PLC attacks - Implement security measures to prevent negative consequences!" Based on the report ...
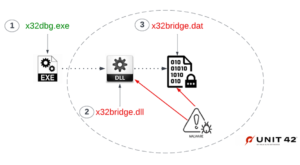
Researchers Discover New PlugX Malware Variant Spreading via Removable USB Devices
"This PlugX variant is wormable and infects USB devices in such a way that it conceals itself from the Windows ...

New attacks use Windows security bypass zero-day to drop Qbot malware
New phishing attacks use a Windows zero-day vulnerability to drop the Qbot malware without displaying Mark of the Web security ...

What is Triton malware and how it works
Introduction Triton malware is a type of malicious software that is designed to target industrial control systems (ICS). It is ...

Hacker-made Linux Cobalt Strike beacon used in ongoing attacks
Cobalt Strike is a commercial penetration testing tool, which gives security testers access to a large variety of attack capabilities ...
Malware Hidden In GPU Memory, Invisible to Antivirus Applications, Could Potentially Harm PCs
Criminals in cyberspace have created a malware program that can be hidden in GPU memory and make it invisible to ...

The U.S. food supply is not cyber-secure or safe from threats to control systems
The U.S. Food and Drug Administration (FDA) issued the final rule on the Food Safety Modernization Act (FSMA) in November ...

Snake Ransomware Delivers Double-Strike on Honda, Energy Co.
The ICS/SCADA-focused malware is likely behind a duo of attacks this week, on Honda and a South American energy company, ...

Power company Enel Group suffers Snake Ransomware attack
European energy company giant Enel Group suffered a ransomware attack a few days ago that impacted its internal network ...


