Security by design is one of the most important and fundamental activities during the process of implementing cybersecurity in industrial systems. Security by design should be performed after detailed cyber risk assessment according to the requirements of ISA/IEC-62443-3-2 “Security Risk Assessment for System Design”.
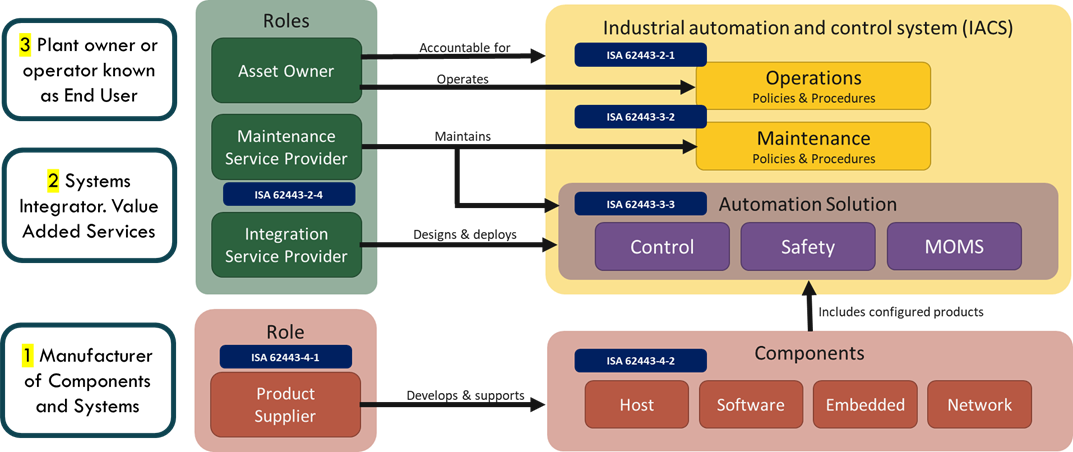
Within ISA/IEC62443 series of standards there are three lavels of security-by-design. (1) Component manufacturer, (2) Value-added solution or service provider, and (3) Plant owner or operator. These with the three main roles that are identified in the ISA/IEC-62443 series of standards. In fact, each of these roles should develop its own cybersecurity management system or CSMS (Cyber Security Management System).
The Design of the Products or Components (1)
Design of the product or component by the manufacturer. The manufacturer of the component, whether it is hardware or software, must design it to meet the security requirements depending on whether it is SL 1, 2, 3 or 4. This with a view to the certification of the component or system, understanding a system as the combination, assembly and configuration of multiple components. In this case, the target security level (SLT) is a decision of the manufacturer.
The manufacturer must first incorporate security into its management system, accompanying the entire life cycle of each of the components. To do this, it must first certify the management process according to the requirements of the ISA/IEC-62443-4-1 standard.
Once the user has incorporated and certified the implementation of the ISA/IEC-62443-4-1 standard, you can apply to individually certify each of the components that it produces, being able to freely choose any of the security levels 1, 2, 3 and 4. It is the manufacturer’s decision to define its strategic positioning in terms of cybersecurity and it will do so according to the demand of its current or potential customers.
Four types of components are identified. Depending on the type of component and the target level of security that the manufacturer wishes to certify, they will have specific security requirements. These components shall be designed by the manufacturer in accordance with the requirements of the ISA/IEC-62443-4-2 standard.
This is perhaps the easiest security by design for most professionals and companies to understand, although it is not the easiest to implement. The manufacturer must first develop and certify a mature CSMS management system (ISA/IEC-62443-4-1), and then be able to certify its components (ISA/IEC-62443-4-2). The companies that have decided to reach this level have an arduous road to travel, which will take no less than several years.
This is where ISASecure comes into play with all its certification programs. Manufacturers will eventually need to hire a certificate authority to first audit their internal processes. Once certified, they must contract with the same or another certification authority to certify their products and systems.
ISASecure defines the requirements that must be met by certificate authorities as certified companies. ISASecure defines a certification scheme. WisePlant has been an active member of ISASecure since 2022. We are active supporters and promoters of the activities carried out by ISASecure.
For manufacturers who want to get certified, I recommend that they take the IC47 course, official ISA. Or we at WisePlant can provide consulting services to help the manufacturers to develop the management program to get ready to obtain the certification. Contact us to know more about it.
The design of the Systems Under Consideration – SUC (2)
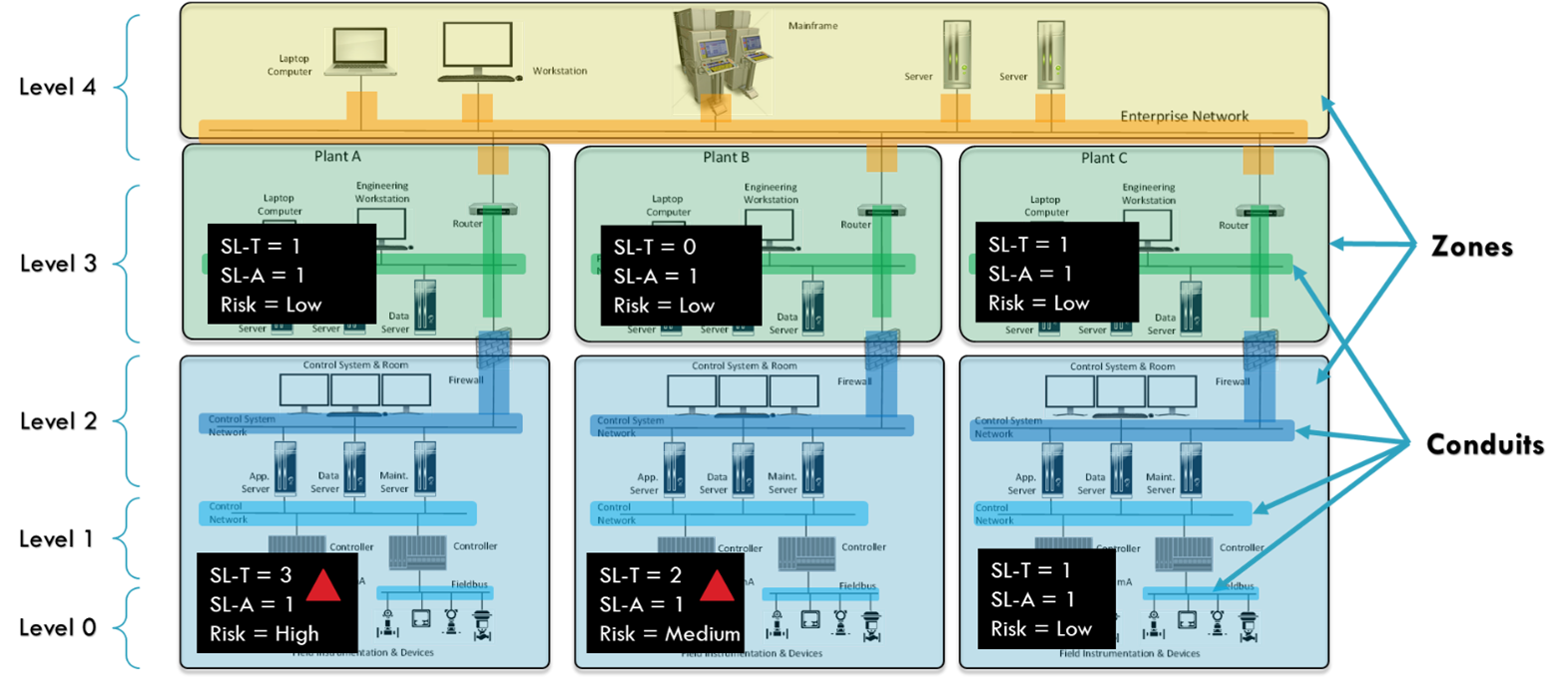
Design of the control system to meet cybersecurity requirements and/or specification . Generally, the system is visualized and managed as a set of zones and conduits (node), where each node will have a specific set of security requirements that the supplier must meet.
You can see from the first diagram that two types of value-added service providers are distinguished. The system integrator (new systems), the provider of maintenance services on existing systems in the plant.
In this case, the value-added service provider is the one who must design the new system or redesign the existing system in the plant to meet the specific and particular requirements of each zone and conduit. It should be noted that a system can meet security requirements without the need for all its components to be individually certified.
If the products individually or the system meet the security requirements because they were already certified by the manufacturer, so much the better. Finally, this should be the most economical solution for the end user. Otherwise, the value-added service provider will have a harder task and will need to add additional components to compensate for the lack of security already available.
In the case of a new system, it is the system integrator, or the provider of the turnkey solution who must design the security according to the security specifications of the buyer, his client. In this case, the end user carried out the risk assessment before going out to buy the new system and gave their supplier a set of functional specifications (as they always did), plus a new set of technical security specifications.
For existing systems, the end user will work in conjunction with the value-added service provider to make changes as needed. Some changes may be introduced by the end user, while other changes may be introduced by service providers. In this case, the security project manager plays a fundamental role for an effective and efficient implementation of security.
In any case, it is necessary to incorporate security by design. This is one of the most complex tasks in effective risk mitigation. In general, companies repeatedly fail to interpret the results of the risk assessment, and its design before starting to implement changes. They rush to introduce changes without proper design. Invariably this leads to making many mistakes due to lack of experience or lack of understanding of the ISA/IEC-62443 requirements.
The design of the plant (3)
The solution design at the plant level. To the above is added a set of administrative, procedural, physical and mechanical requirements. It may even be necessary to modify the industrial process by design to mitigate cyber risks.
This is where it is vitally important that design activities are carried out correctly. Whether for a new system under construction, or for an existing system. The secure design must be developed in a manner consistent with the plant’s other risk disciplines, policies, and procedures. In addition to physical security.
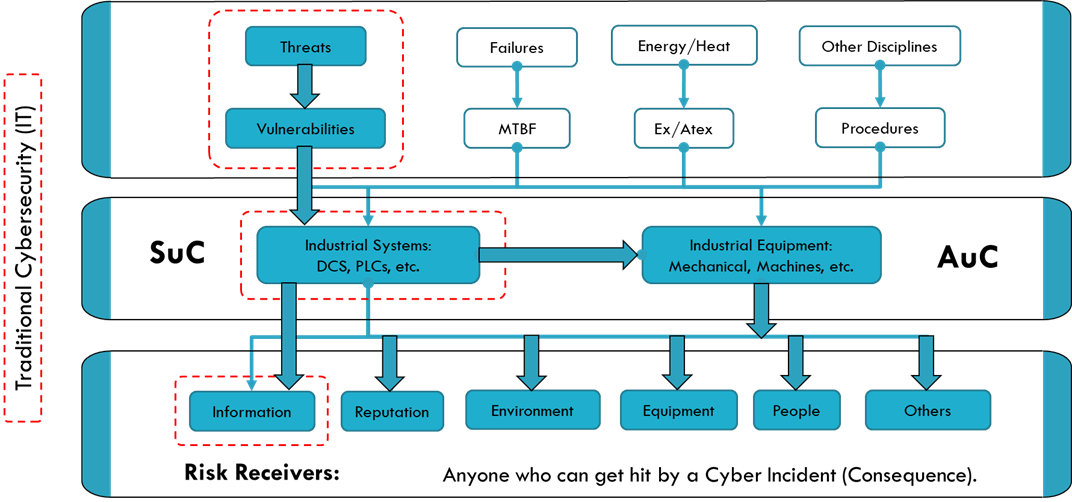
The multiple disciplines of industrial risk have common objectives. Avoid the occurrence of the same potential consequences, of different causes or motives. Improving one risk discipline to the detriment of the other is not a benefit for the industrial plant. The design must be consistently implemented.
Two zones with the same SLT security level can have very different security requirements. What we call adjusted SLT (Vector SLT), or particular security specifications for each of the nodes. Many organizations skip this step and lose their way to security.
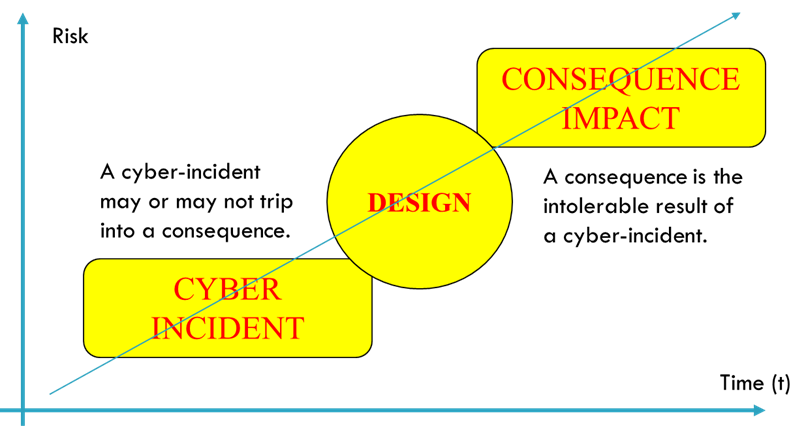
The end user is more concerned or should be more concerned about mitigating the probability of occurrence of the consequence than of the cyber incident. This is where most organizations are failing. The cyber incident is something that happens to the control system, while the consequence is something that happens to the plant. The cyber incident without consequence does not pose a risk to the plant.
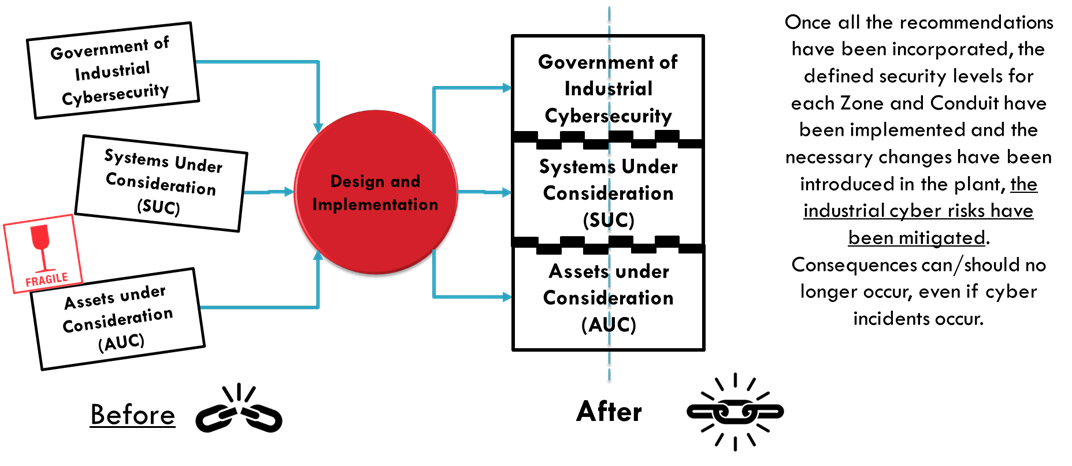
A robust and secure design of the control system and the plant means that consequences are prevented and avoided, even if cyber incidents do end up occurring. In other words, the plant tolerates the occurrence of the cyber incident. Even if it makes an effort to protect cyber assets, the cyber incident will end up happening. It will be less likely, but it will end up happening.
Robust design goes beyond preventing the occurrence of the cyber incident, preventing the occurrence of the consequence. This is what we call security by design at the plant level. Many believe that technology has all the answers to security, and this is false.
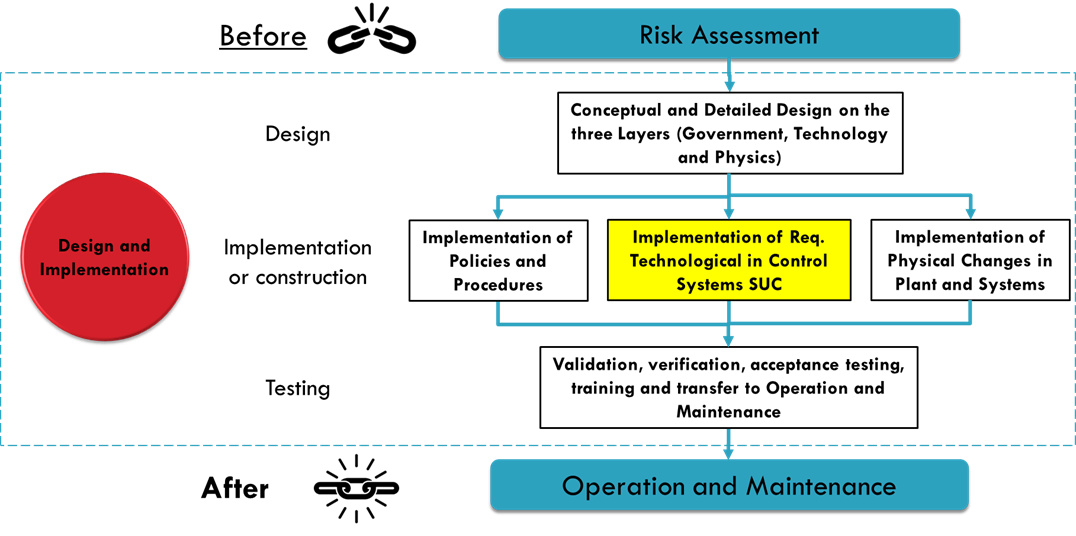
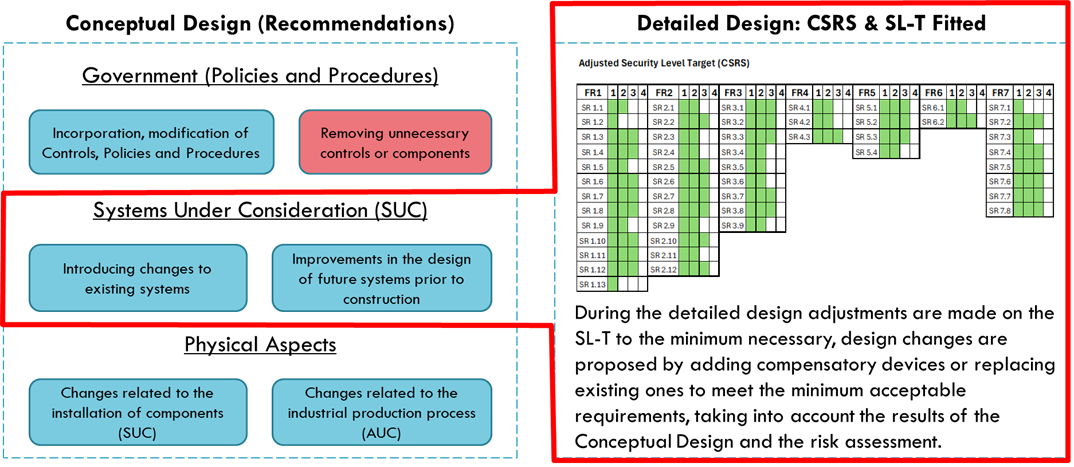
Conceptual Design
The conceptual design allows the plant to consistently implement the recommendations that are produced because of the detailed risk assessment, while influencing the design of the control and safety systems with the design of the plant, including the governance.
Detailed Design
The detailed design of the zones and conduits should be the result of the risk assessment. In this case, the SLT is adjusted according to a series of rationales that were produced during the risk assessment and the particular characteristics of each node and its essential functions. This is how two nodes with the same SLT can have a set of different security requirements.
It is of fundamental importance to understand the industrial process and the potential intolerable consequences that must be avoided. Many companies with reputable expertise in information security skip this entire process by ignoring the particular context of each zone and conduit, implementing “security controls” that do not fit with the risk assessment. This results in a significant portion of the budget being spent on security measures that do not mitigate risk. They only mitigate the budget.
Security requirements for zones and conduits are defined in the ISA/IEC-62443-3-3 standard. These requirements can be met in different ways. It will be the responsibility of whoever is in charge of the design to select the way in which each of these requirements will be met.
Responsibility for the design of security in IACS/SUC industrial systems should be carried out by professionals who understand the outcome of the risk assessment, the requirements of the ISA/IEC-62443-3-3 standard, and the industrial context in which it should operate. Some of the three roles may be applicable:
- Provider of turnkey solutions for the supply of new systems. It is when the system integrator builds a new system according to cybersecurity specifications developed as a result of a risk assessment.
- Value-added service providers working on existing systems in industrial plants. In this case, suppliers influence the design of the existing system and the plant to mitigate the risks that were identified in each of the industrial processes.
- The owner of the industrial plant acts as his own integrator. It is very common for industrial plants to have engineering and maintenance personnel acting as their own integrators, in charge of the maintenance of their systems.
Whatever the case, they must develop good security by design practices in their engineering or reengineering processes. Failure in this process means a failure to mitigate risks.
In the case of WisePlant, in the WBS methodology, we incorporated what we call Secure & Protect®, an exclusive and consistent methodology to influence the design of the system and the design of the plant. It allows to ensure a design of cybersecurity in industrial systems throughout the life cycle of the IACS/SUC system.
The design of cybersecurity must be such that it allows the following requirements to be met:
- Correctly interpret the results of the detailed cyber risk assessment. The methodology must comply with the requirements of the ISA/IEC-62443-3-2 standard. The results will produce a series of rationales that will be used during the design activities. The following main design activities are distinguished:
- Conceptual Design.
- Detailed design.
- Rationalization.
- Implement mitigation measures to avoid the occurrence of potential consequences. All those consequences that were identified during the risk assessment. Mainly those that are not tolerable by the organization.
- Reduce the probability of occurrence of cyber incidents according to the objective security levels (SLT), which have been mapped to the plant’s industrial risk matrix.
- Assist in the safe and secure operation of the plant. Develop the capacity to recover from potential cyber incidents as soon as possible according to the needs and priorities of each zone and conduit. While cyber incidents can no longer produce unacceptable consequences for the organization, this does not mean that cyber incidents no longer matter.
- Implement preventive and corrective maintenance activities to maintain security in each of the zone and conduit.
- Develop continuous improvement practices. Audit and verify compliance through documented and traceable practice. To maintain records that allow history to be retained and to preserve the knowledge that is the result of the experience acquired day after day.
Maximizing the return on investment in industrial cybersecurity. Avoid the occurrence of potential consequences at the lowest possible cost by making long-term decisions. That is, risk mitigation decisions that last over time. The robust design of security plays a key role in this goal. Design methods that have as their fundamental premise to avoid the occurrence of the potential consequence, even if the cyber incident still occurs, will produce the most durable and best results for the organization. Creating a resilient organization.
The Foundational Requirements
The 7 FRs. The ISA99 committee, after much debate and analysis, concludes that the security triad is insufficient to manage security in areas and pipelines. They conclude seven foundational requirements. These foundational requirements move freely according to the design conditions and rationale that was produced during the risk assessment. The SLT becomes a cybersecurity vector adjusted to the particular conditions.
- FR1 = Access Control (IAC)
- FR2 = Usage Control (UC)
- FR3 = System Integrity (SI)
- FR4 = Data Confidentiality (DC)
- FR5 = Restrict Data Flow (RDF)
- FR6 = Timely Event Response (EROI)
- FR7 = Resource Availability (RA)
Requirements vs. Controls. The ISA/IEC-62443-3-3 standard produces a list of design requirements that the person responsible for the design of the zones and conduits will have to see how it manages to meet these requirements. The first thing is to interpret them correctly. To do this, you will need to select the components, assemble them and configure them in a specific way. Finally, it is the responsibility of the end user and/or value-added service provider to select controls to verify and/or validate that each zone and conduit meets design requirements. Design requirements and security controls are not the same thing. Two sides of the same coin, but two different things that most of the audience still do not understand.
Rationalization
Rationalization is a technique to design the monitoring, detection, alarming, and response system in a such a way that only meaningful alarms are produced avoiding the generation of false alerts/alarms which does not create any value to the organization and only cause distraction of valuable plant resources. This will be a topic for another article.
Capabilities that a supplier must develop
The value-added service provider must develop the capabilities as defined in the ISA/IEC-62443-2-4 standard. The supplier must also develop a CSMS management system with all its security practices documented, traceable and auditable. Many still believe that having certified staff is enough, which is just the beginning. This will be a topic to be developed in another article.
Training and certification programs in industrial cybersecurity
The best training program to understand the ISA/IEC-62443 series of standards is the official ISA courses. The course known as IC34 includes the foundations for understanding design activities. However, this course does not go into the detail of each of the requirements, nor does it teach various design techniques. In addition, it covers implementation and acceptance testing aspects.
To develop design activities and master the technique in depth, WisePlant has recently created the 2170/EN70 Course. More information is available at WiseCourses.com.
EN70: Security By Design for Control Systems Engineers and Service Providers
- Objective: Explains security by design at the SuC level for energy, oil, and gas sectors.
- Focus: Compliance with ISA/IEC-62443 standards, including detailed cybersecurity requirement specifications. Harmonize with popular regulations (NIST, NERC, C2M2, etc.)
- Skills: Engineers learn to design control systems to meet security requirements, interpret risk assessments, and select appropriate components.
- Outcome: Ability to perform conceptual and detailed designs, rationalize, determine security levels, and create Cybersecurity Requirements Specifications (CSRS).







Get Involved & Participate!
Comments