Preventive and Corrective Actions for Sustained OT Security
In industrial plants, the concept of maintenance is well established—equipment must be regularly inspected, repaired, and updated to ensure safe and reliable operations. But as digitalization continues to expand across Operational Technology (OT), cybersecurity also requires proactive maintenance.
Just like physical assets, digital systems degrade, become outdated, or get misconfigured over time. And when they do, they expose the plant to cyber risks that can disrupt operations, compromise safety, or enable attacks.
It’s time we treat cybersecurity maintenance as part of standard plant operations.
The Case for Cyber Maintenance
Industrial cybersecurity isn’t just about firewalls and antivirus. It includes:
- Controllers and HMIs with aging firmware
- Network devices with outdated configurations
- Unpatched vulnerabilities in OT software
- Weak or unused credentials lingering in control systems
- Logging systems that silently stop capturing data
- Security functions and strategies to mitigate localized risk.
Each of these is a point of failure—unless managed like any other operational asset.
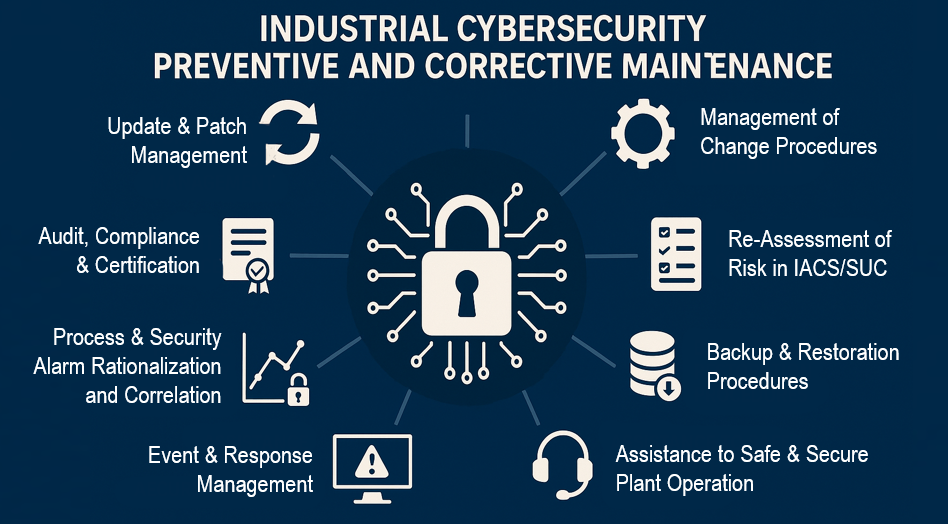
Preventive Cybersecurity Maintenance: Stay Ahead of the Risk
Preventive actions are those done to mitigate identified risk, aimed at keeping the system resilient and compliant. Change management procedures is the most important procedure that should not be bypassed by any chance. Evaluate the risk of changes before approving and moving forward, as the security level and key security functions and strategies many need to be changed.
Key preventive cyber maintenance tasks include:
- Change Management Procedures, evaluate changes before approval
- Patch and firmware management for PLCs, RTUs, HMIs, servers
- User account reviews: remove unused or expired accounts
- Credential rotation: change passwords regularly on all critical systems
- Backup validation: test that backups are current and restorable
- Firewall and switch audits: check for unauthorized rule changes or drift
- Log review and system health checks for SIEMs and anomaly detectors
- Asset inventory reconciliation to detect unauthorized devices
This work needs to be scheduled, documented, and coordinated with operations to avoid unintended downtime.
Corrective Cybersecurity Maintenance: Recover and Harden
Corrective actions are taken after a deviation is detected, such as:
- A cyber-incident.
- A failed authentication event.
- A detected malware signature.
- A configuration found to violate security policy.
- An unexpected system shutdown due to overload or attack.
Effective corrective cyber maintenance includes:
- Incident containment and recovery (isolation, reimaging, restoring backups).
- Post-incident review and hardening (closing the gap that was exploited).
- Configuration rollback and system revalidation.
- Documentation updates and lessons learned for future defenses.
Corrective maintenance is more than response—it’s an opportunity to build future resilience.
Embedding Cyber Maintenance Into Plant Culture
To be effective, cybersecurity maintenance must be treated like physical maintenance:
- Logged in the CMMS or OT asset management system
- Assigned to responsible personnel (IT/OT/security roles)
- Supported by procedures, training, and scheduled windows
- Measured and reviewed regularly
Cyber maintenance isn’t a project. It’s a discipline—and it protects not just data, but physical operations, safety systems, and reputational trust.
Conclusion: Secure Systems Require Ongoing Care
Cybersecurity in OT require regular attention to stay safe and functional.
By formalizing preventive and corrective cybersecurity maintenance, industrial plants can reduce risk exposure, improve detection and response, and sustain operational trust in a connected world.
Is Cybersecurity Part of Your Maintenance Plan?
Are your teams maintaining digital systems with the same discipline as physical ones?
Let’s share practices that help make cybersecurity operational—not just technical.




Get Involved & Participate!
Comments