The clip discusses the challenges of calculating industrial cybersecurity risk, emphasizing the importance of understanding and effectively implementing risk formulas, highlighting the role of system design in preventing cyber incidents, and stressing the significance of informed decision-making and proper investment in cybersecurity solutions.
Author: Maximillian G. Kon
Episode 2 Clip 2 – The true goals of industrial cybersecurity.
This clip discusses the importance of industrial cybersecurity in preventing consequences rather than just incidents. It emphasizes the need for strategic management of risks to ensure plant safety and longevity, highlighting the key role of correctly implemented cybersecurity measures. The video also touches on calculating return on investment and the significance of maintaining a comprehensive cybersecurity strategy for overall business success.
Episode 2 Clip 1 – The importance of Risk Assessment.
This video cast focuses on the importance of risk assessment in industrial cybersecurity. The speakers discuss the significance of identifying and mitigating intolerable risks through proper risk assessment practices. They emphasize the different disciplines of risk present in typical plants and stress the need for accurate decision-making based on sound analysis.
Episode 2 – Mastering Industrial Cybersecurity Risk Assessments
This episode features a discussion between Angel Lopez and Max Kon about industrial cybersecurity risk assessment. Max highlights the importance of making the right decisions as it would most probably be the only and the best chance that the plant may have. The need to use the resources of the company wisely is not an option. Furthermore, it is not about money, it is about time and opportunity.
IEC publishes IEC 62443-2-1:2024, setting security standards for industrial automation and control systems
Addressing cybersecurity on an organization-wide basis can seem like a daunting task. There is no simple cookbook for security, nor is there a one-size-fits-all set of security practices. There is a methodology for implementing ISA/IEC-62443 series of standards correctly. It is paramount that end users, integrators and suppliers get involved.
About Maximillian G. Kon
A U.S. citizen born in Memphis, Tennessee, with residency in Argentina and Brazil, Max is founder and CEO of WisePlant HQ. He is an Electronics Engineer with specialization in control systems and telecommunications and has developed his professional career mostly in South America, with more than 20 years of experience in industrial and critical systems in all types of industries, including oil, gas, energy, food, pharmaceutical, chemical, petrochemical, water, paper, metallurgy, mining, smart buildings, and others.
WisePlant Group LLC & WiseCourses LLC Announces Commitment to Growing Global Cybersecurity Success during Cybersecurity Awareness Month October 2024
Now in its 20th year, Cybersecurity Awareness Month October 2024 is highlighting the growing importance of cybersecurity in our daily lives and encouraging individuals and industries to take important industrial cybersecurity steps to keep plants safe and control systems secure. Empowering more secure, interconnected industrial plants.
New ISAGCA whitepaper addresses zero trust outcomes using ISA/IEC 62443 standards
Discover how the new ISAGCA whitepaper leverages ISA/IEC 62443 standards to achieve zero trust outcomes and enhance cybersecurity excellence.
Episode 1 – Introduction to Industrial Cybersecurity
This episode features a discussion between Angel Lopez and Max Kon about industrial cybersecurity. Max highlights the importance of ISA standards in industrial automation and cybersecurity, emphasizing his active involvement in ISA activities and training programs. Max’s journey underscores the evolution of cybersecurity in control systems and his dedication to promoting cybersecurity awareness and standards within the industry.
Episode 1 Clip 6 – What are the best training courses or programs for End Users and Providers?
Emphasizes the importance of investing in cybersecurity training programs, particularly the official ISA certificate training and the WisePlant cybersecurity program. It highlights the need for understanding and implementing cybersecurity requirements correctly, tailored to individual roles. The training aims to ensure project success by aligning all participants towards a common goal in the cybersecurity field.
Episode 1 Clip 5 – What do you think is the most difficult challenge to manage or mitigate the industrial cybersecurity risk?
Discusses the challenges of managing industrial cybersecurity effectively, emphasizing the importance of doing the right things correctly. It highlights why companies struggle with implementing standards and how viewing cybersecurity as an investment, rather than an expense, is crucial for the long-term security and success of businesses.
Episode 1 Clip 4 – What are the most common mistakes that you’ve seen in the market so far?
Outlines common mistakes in industrial cybersecurity, including skipping risk assessments, copying IT security policies without adaptation, and relying solely on employee training. Practical advice is given on how to prevent these errors and improve cybersecurity practices.
Episode 1 Clip 3 – What is the best approach to address industrial cybersecurity?
Emphasizes the necessity of a continuous cultural change towards cybersecurity in industrial operations for end users, service providers, and manufacturers. It highlights the importance of implementing cybersecurity management programs, conducting risk assessments, mitigating risks, and maintaining long-term security measures across the entire supply chain.
Episode 1 Clip 2 – What is the main difference between IT and OT security?
Discusses the significant differences between IT and OT security. It highlights key distinctions such as availability, technology lifespan, and the primary focus of preventing cyber incidents in IT and preventing consequences in OT environments. The crucial dissimilarity lies in managing risks: IT focuses on preventing incidents, while OT prioritizes preventing consequences.
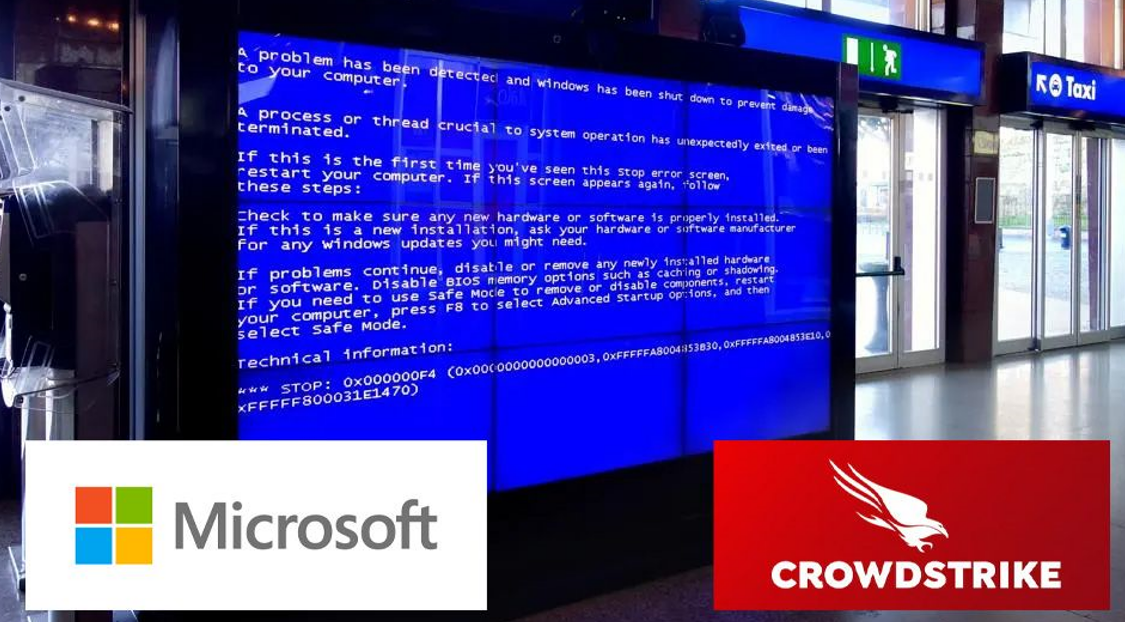
What can we learn from the 2024 CrowdStrike incident towards industrial cybersecurity?
CrowdStrike, an American cybersecurity firm, released a configuration update for its Falcon sensor software that inadvertently triggered a catastrophic chain reaction.
Episode 1 Clip 1 – Tell us about yourself
Max shares his experiences working in the industrial automation field, collaborating with the International Society of Automation (ISA), and transitioning into cybersecurity. He highlights the importance of ISA standards in industrial automation and cybersecurity, emphasizing his active involvement in ISA activities and training programs.
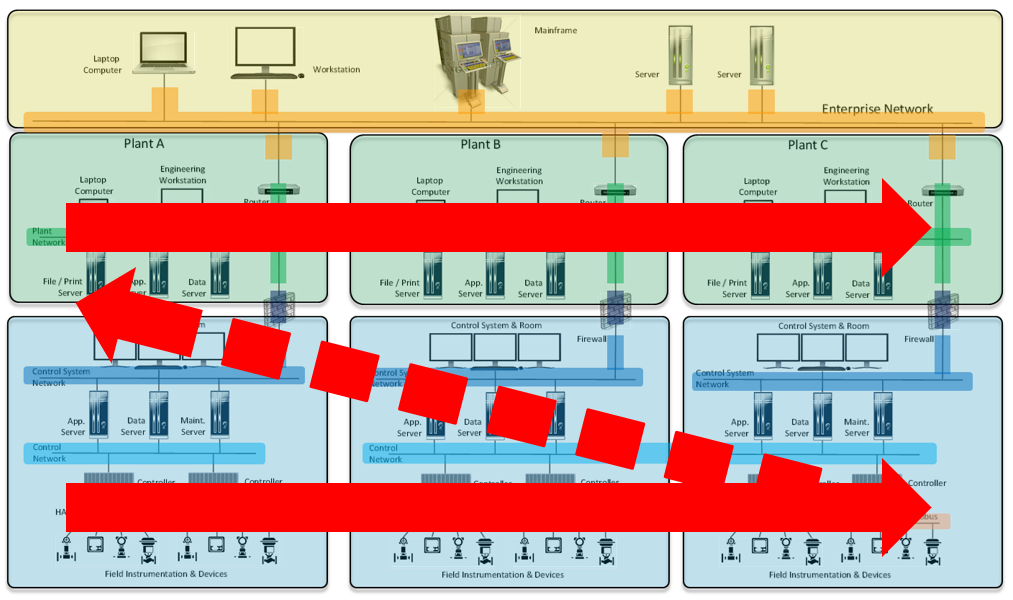
Understanding Zones and Conduits
Every professional who designs configure and maintain any type of control systems, need to learn about zones and conduits and manage the new security requirements and develop necessary skills according to their function, even if they are not into industrial cybersecurity.
The State of Knowledge and Risk Management in Industrial Cybersecurity (ISA/IEC-62443-3-2)
The state of knowledge in industrial cybersecurity during the past decade is based on a vast experience. There is a lot more to come soon.
Rationalization: Stop spending valuable resources wrongly
We see very often how companies (through their security staff) go shopping and rush to spend, often pushed by the pressure of the business, the inertia of the market, lack of knowledge, skill and opportunism of suppliers, before performing a good risk assessment.
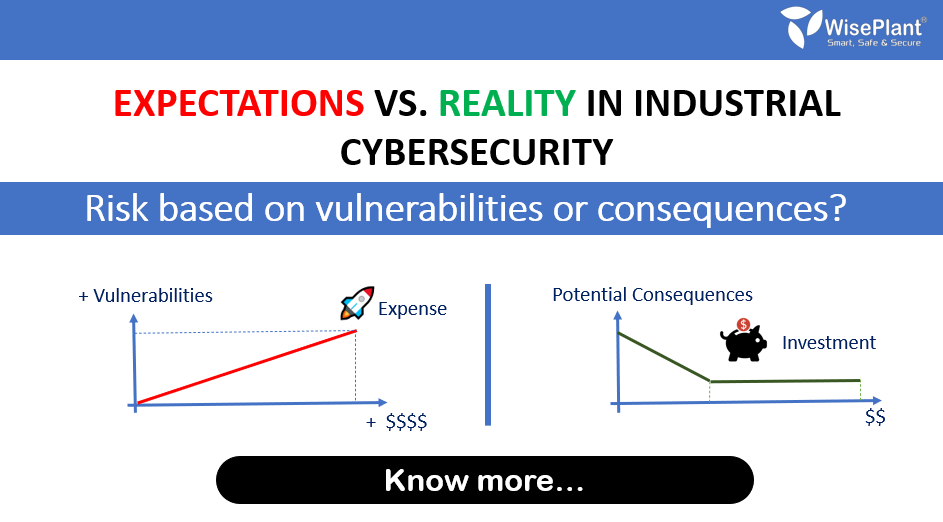
Industrial cyber risk management based on vulnerabilities or consequences?
We have already talked about the need to perform an industrial cyber risk analysis, and this time we will address one of the mistakes most commonly assumed "and accepted" by enthusiasts in industrial cybersecurity. Risk analysis based on vulnerabilities or consequences?