We see how many professionals with vast experience in Information Security, industrial companies that take action, renowned cybersecurity consultancies, government organizations and technology developers are mistaken (by far) in defining the objectives for their industrial cybersecurity strategy. Clearly defining goals is the first big step before starting this big change.
Bad decisions. Wrong Priorities. Incorrect and Insufficient.
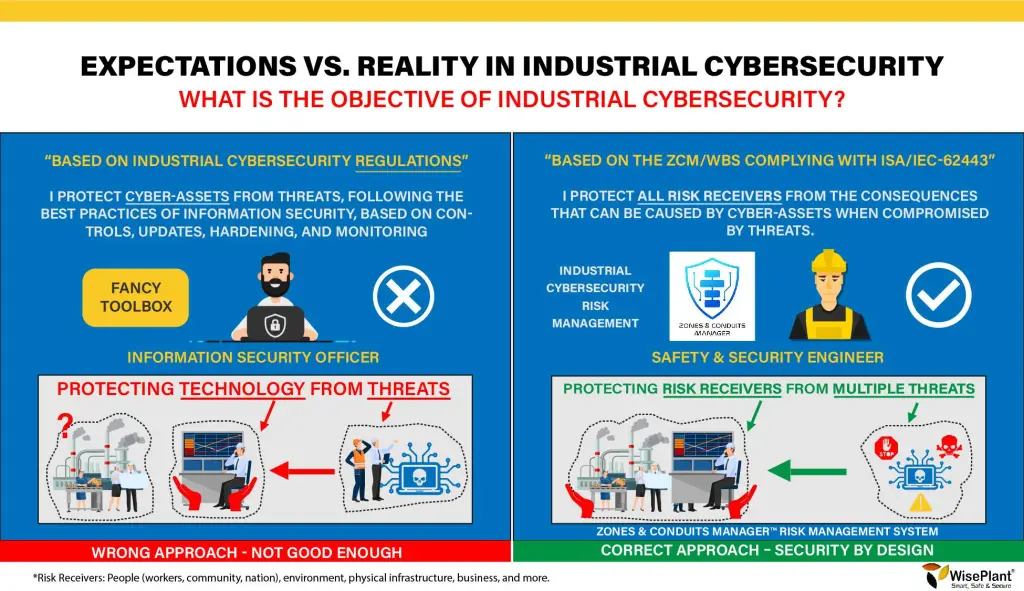
- Most organizations work on the wrong working hypothesis, assuming that “If they protect Cyber-Assets, then they protect people, the environment, etc.” This working hypothesis is incorrect.
- The bases of the Industrial Cybersecurity Program are structured on the wrong columns.
- It’s like planting a big tree (which will grow) inside a small pot. It will fall under its own weight.
- Prioritizing security actions the wrong way.
- Not knowing what you want or should protect.
Security by Design. Correct and Enough.
- Identify all risk recipients in the event that cyber-assets are compromised.
- Define a methodology for risk assessment that allows decisions to be made based on the consequences that could affect all risk recipients.
- Redesign or design industrial systems and plants that are sufficiently resilient so that even though cyber-assets are compromised, they cannot affect risk receptors, security by design.
The vast majority are not responding well to these questions. What are we protecting? Do we protect cyber assets? Sure?
Incorrect: Many believe that if we protect cyber assets, then we protect people, the environment, and more. This working hypothesis is incorrect and far from reality. Cyber assets are being given higher priority than human lives.
Correct: protect all risk receptors. Prevent consequences from occurring even if cyber assets are compromised. In an extreme situation we are willing to lose a cyber asset, but we are not willing to lose a human life. At least that’s how it should be.
It is a mistake that the vast majority of professionals, especially those specialists in information security, make. Unfortunately,
they have overly influenced governments and company CEOs to make the wrong decisions and have created regulations that fail to protect risk-takers or are insufficient. They protect man’s cyber assets, instead of protecting man from vulnerable cyber assets.
The vast majority are not responding well to this question. Why do we want or should we deal with Industrial Cybersecurity?
Incorrect: we are protecting cyber assets, your information and the data inside them because it is the most important thing for my organization. This may be correct for corporate systems from a business perspective, and is typical for information security professionals. It is incorrect from the perspective of industrial processes.
Correct: we are protecting all risk recipients and preventing consequences in the physical world from occurring. The effects of industrial cyber assets, once compromised, can have consequences outside of them and not inside. The vast majority of the time, data inside industrial cyber assets is irrelevant.
Industrial cyber assets are immersed in a physical world, where what we want and must protect is outside of them. OT is the domain of physical security. IT is the domain of information security. There are many significant differences between IT and OT. Different problems require different solutions. Very different!
The vast majority are not responding well to this question. What should we get as a result?
Incorrect: prevent cyber assets from being compromised by cyber threats. Protect cyber assets from the same threats that affect information systems. They approach industrial cybersecurity in the same way as information security. They prioritize over those cyber assets that connect to the network or networks.
Correct: control industrial cyber risk to the limits tolerable by the organization. Prevent the occurrence of all the consequences identified in the domain of physical security that can affect all internal and external risk recipients of the organization, including the business. Do not underestimate any component.
All assets that are cyber sensitive must be analyzed, whether they are connected or disconnected from networks. Any cyber sensitive component must be analyzed from the perspective of the recipients of risk and not only from the perspective of business and information security.
The vast majority are not responding well to this question. Does our program meet the objectives?
Incorrect: if the goals are poorly defined, we can meet the wrong goals perfectly well. Fulfilling the wrong objectives perfectly can be irrelevant.
Correct: once the objectives are well-defined, it is a matter of doing the right things, correctly implementing the correct rules, correct procedures, etc. Do things right.
Implement the correct rules correctly. Many times it is observed that organizations do not understand the standards. As a first step, the objectives must be well defined.
The vast majority are not responding well to this question. What is an industrial cyber incident?
Incorrect: When an information security system is implemented, cybernetic events are considered to be all those that compromise or may compromise confidentiality, integrity or availability, without knowing the potential consequences in the physical world.
Correct: industrial cyber incidents are those that have some potential to cause a consequence that affects risk recipients. It requires identifying cyber events in context with the physical world and real risk.
This is one of the most common and common errors. When an information security system is implemented, cyber events are considered as incidents. This is incorrect. Cyber events or typically considered incidents from an information security perspective are insignificant and unimportant in the physical security domain. Too many false positives are generated without response, many unnecessary and expensive activities that serve no purpose.
The vast majority are not responding well to this question. How are we making decisions?
Incorrect: use the wrong methodology. Many organizations are used to using statistical data and vulnerability studies to make decisions to mitigate industrial cyber risks. Both criteria are wrong and will lead to wrong decisions, waste of money and insufficient solutions.
Correct: use a decision-making methodology that meets RAGAGEP requirements and the ISA/IEC-62443-3-2 series of standards. All risks unacceptable by design are mitigated with long-term decisions, independent of new vulnerabilities and new threats.
The wrong methodology automatically means making poor decisions. The correct methodology means making good decisions.
What ends up happening? The sad reality:
Incidents keep happening.
Wrong Prioritization.
They spend much more money than necessary.
They take incorrect security measures.
Security actions are insufficient.
They implement short-term solutions.
They don’t solve the problem.
Some are making it. What it should be?
Unacceptable consequences can no longer occur.
They prioritize cyber assets correctly.
They invest what is fair and necessary.
They make correct, effective and efficient decisions.
Sufficient security actions.
They implement long-term solutions.
They solve the problem.





Get Involved & Participate!
Comments