Industrial cybersecurity is one of the industrial risk disciplines with the ultimate objective to protect industrial assets and to prevent intolerable potential consequences from happening. Typically, there are many disciplines of risk on industrial plants, such as, people safety, environmental safety, intrinsic safety, functional safety, and more. They all share the same objectives, such as protecting physical assets.
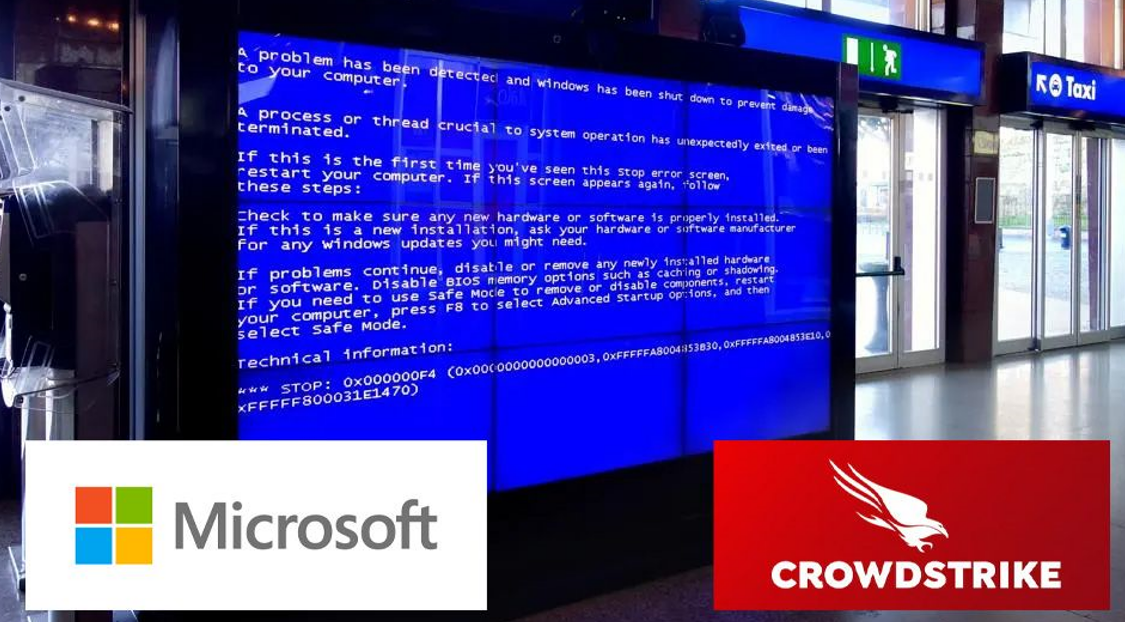
What can we learn from the 2024 CrowdStrike incident towards industrial cybersecurity?
Maximillian G. Kon
July 26, 2024
0
CrowdStrike, an American cybersecurity firm, released a configuration update for its Falcon sensor software that inadvertently triggered a catastrophic chain reaction.
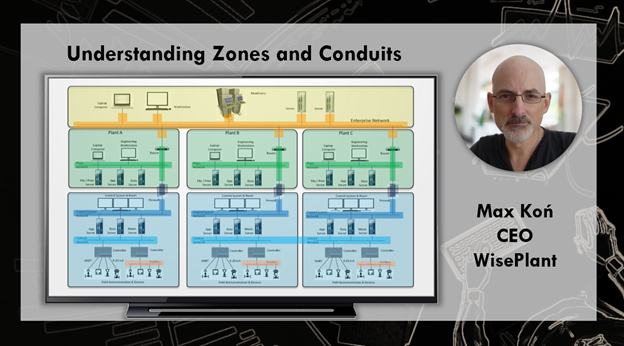
Understanding Zones and Conduits
Maximillian G. Kon
December 27, 2023
0
Every professional who designs configure and maintain any type of control systems, need to learn about zones and conduits and manage the new security requirements and develop necessary skills accordin...
CISA warns of actively exploited Juniper pre-auth RCE exploit chain
Max K.
November 20, 2023
0
In addition, CISA is working with Juniper Networks to develop a patch for the vulnerabilities associated with the exploit chain. CISA is also working with other vendors to ensure that their products a...
The State of Knowledge and Risk Management in Industrial Cybersecurity (ISA/IEC-62443-3-2)
Maximillian G. Kon
November 15, 2023
0
The state of knowledge in industrial cybersecurity during the past decade is based on a vast experience. There is a lot more to come soon.
US energy firm shares how Akira ransomware hacked its systems
Max K.
October 27, 2023
0
US energy firm shares details of Akira ransomware attack, including how it infiltrated their systems and the steps they took to mitigate the damage. Learn how to protect your business from similar thr...
BlackCat ransomware uses new ‘Munchkin’ Linux VM in stealthy attacks
Max K.
October 24, 2023
0
BlackCat ransomware has been found to use a new Linux virtual machine called 'Munchkin' to launch stealthy attacks. Protect your data by staying informed and up-to-date on the latest security threats.
Building automation giant Johnson Controls hit by ransomware attack
Maximillian G. Kon
September 30, 2023
0
Johnson Controls, a leading provider of building automation systems, has been hit by a ransomware attack, potentially compromising the security of its customers. The company is working to contain the...
Cuba ransomware uses Veeam exploit against critical U.S. organizations
Max K.
August 25, 2023
0
"Cuba ransomware: Unleashing a Veeam exploit to wreak havoc on U.S. critical organizations."
Industrial PLCs worldwide impacted by CODESYS V3 RCE flaws
Max K.
August 15, 2023
0
Industrial PLCs around the world are vulnerable to CODESYS V3 RCE flaws, potentially leading to serious security risks. Learn more about the potential impacts and how to protect your systems.
Physical attacks on power grid surge to new peak – Power Grid Sabotage
Max K.
July 18, 2023
0
People are shooting, sabotaging and vandalizing electrical equipment in the U.S. at a pace unseen in at least a decade, amid signs that domestic extremists hope to use blackouts to sow unrest.
Cisco warned customers of a high-severity cisco switch vulnerabilities.
Max K.
July 18, 2023
0
Cisco has recently warned customers of a high-severity vulnerability impacting some of its switch models. This vulnerability could allow attackers to tamper with encrypted traffic, potentially leading...
CosmicEnergy ICS Malware Updates
Max K.
June 17, 2023
0
CosmicEnergy ICS Malware is a sophisticated cyber-attack targeting industrial control systems. It is designed to steal data, disrupt operations, and cause physical damage to critical infrastructure. P...
Pemex refinery blaze injures four
Max K.
May 30, 2023
0
"May 23: A Day of Tragedy as Pemex Refinery Blaze Injures Four"
What is Evil PLC attack and how to prevent negative consequences on industrial plants
Maximillian G. Kon
March 10, 2023
0
"Protect your industrial plant from Evil PLC attacks - Implement security measures to prevent negative consequences!" Based on the report created by Team82.
CISA Warns of Flaws in Siemens, GE Digital, and Contec Industrial Control Systems
Max K.
February 10, 2023
0
CISA has issued a warning about critical vulnerabilities in Siemens, GE Digital, and Contec industrial control systems. These flaws could allow attackers to gain access to and manipulate the systems.
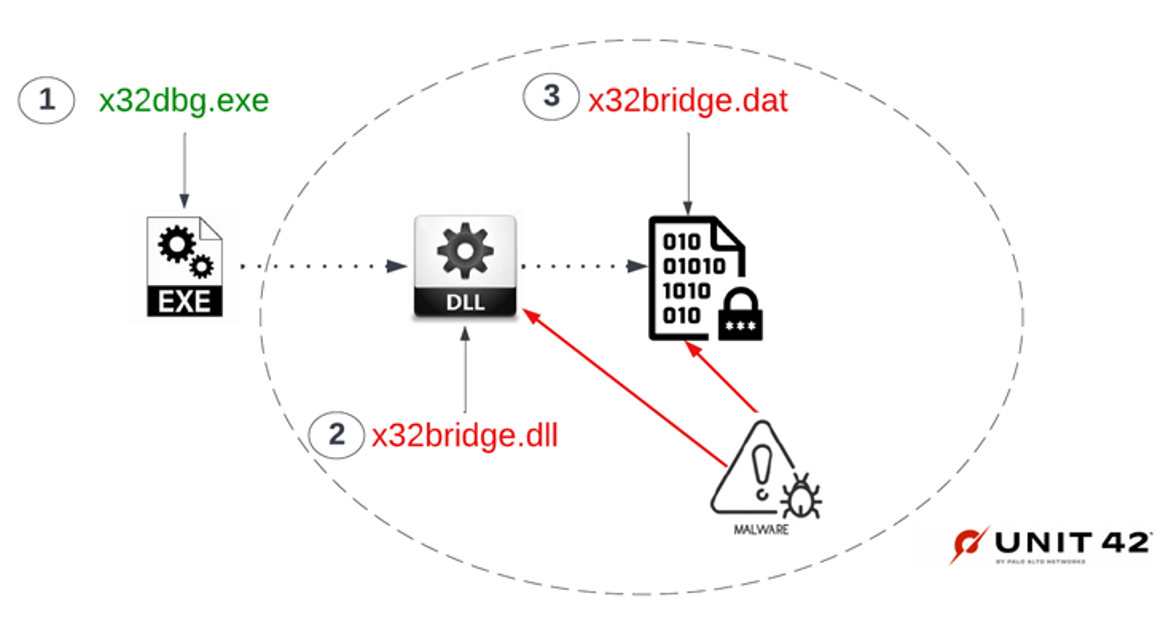
Researchers Discover New PlugX Malware Variant Spreading via Removable USB Devices
Max K.
January 28, 2023
0
"This PlugX variant is wormable and infects USB devices in such a way that it conceals itself from the Windows operating file system," Palo Alto Networks Unit 42 researchers Mike Harbison and Jen Mill...
CISA Alert: Veeam Backup and Replication Vulnerabilities Being Exploited in Attacks
Max K.
January 15, 2023
0
CISA has issued an alert warning of active exploitation of vulnerabilities in Veeam Backup and Replication. Organizations should take steps to protect their systems from potential attacks.
New attacks use Windows security bypass zero-day to drop Qbot malware
Max K.
November 20, 2022
0
New phishing attacks use a Windows zero-day vulnerability to drop the Qbot malware without displaying Mark of the Web security warnings.
Rationalization: Stop spending valuable resources wrongly
Maximillian G. Kon
November 13, 2022
0
We see very often how companies (through their security staff) go shopping and rush to spend, often pushed by the pressure of the business, the inertia of the market, lack of knowledge, skill and oppo...
Construction of Awareness and Training Programs
Ximena Rengifo
August 25, 2022
1
Currently, for companies it is a necessity to develop training and awareness programs in industrial cybersecurity, but there are doubts about how to successfully develop a program focused on generatin...
Digital transformation in industrial cybersecurity
Ximena Rengifo
June 16, 2022
0
In this era of digital transformation, technologies cannot become a pain for organizations, it must be the answer that adds value. That is why it is so important to identify and know the ecosystem in...
Wind turbine firm Nordex hit by Conti ransomware attack
Max K.
April 14, 2022
0
The Conti ransomware operation has claimed responsibility for a cyberattack on wind turbine giant Nordex, which was forced to shut down IT systems and remote access to the managed turbines earlier thi...
WisePlant turns 10!
Max K.
February 28, 2022
0
Today marks 10 years of WisePlant, in our first decade as an independent company, We have strengthened our position in the different disciplines of industrial security, and especially in cybersecurity...
Automation Systems Cybersecurity: From Standards to Practices
Max K.
January 4, 2022
0
Eric Cosman, chairman of ISA99 Committee, explains that standards, guidance, and direction are available from several sources, but surveys and anecdotal reports have shown that many still struggle wit...
Working with future and new systems (Special Edition)
Max K.
December 7, 2021
0
When the owner of the industrial plant has the possibility of having the best of both worlds, the best control systems and the best security. When the consequences occur the damage is done, and there...